AI in Penetration Testing
The Rise of AI in Penetration Testing
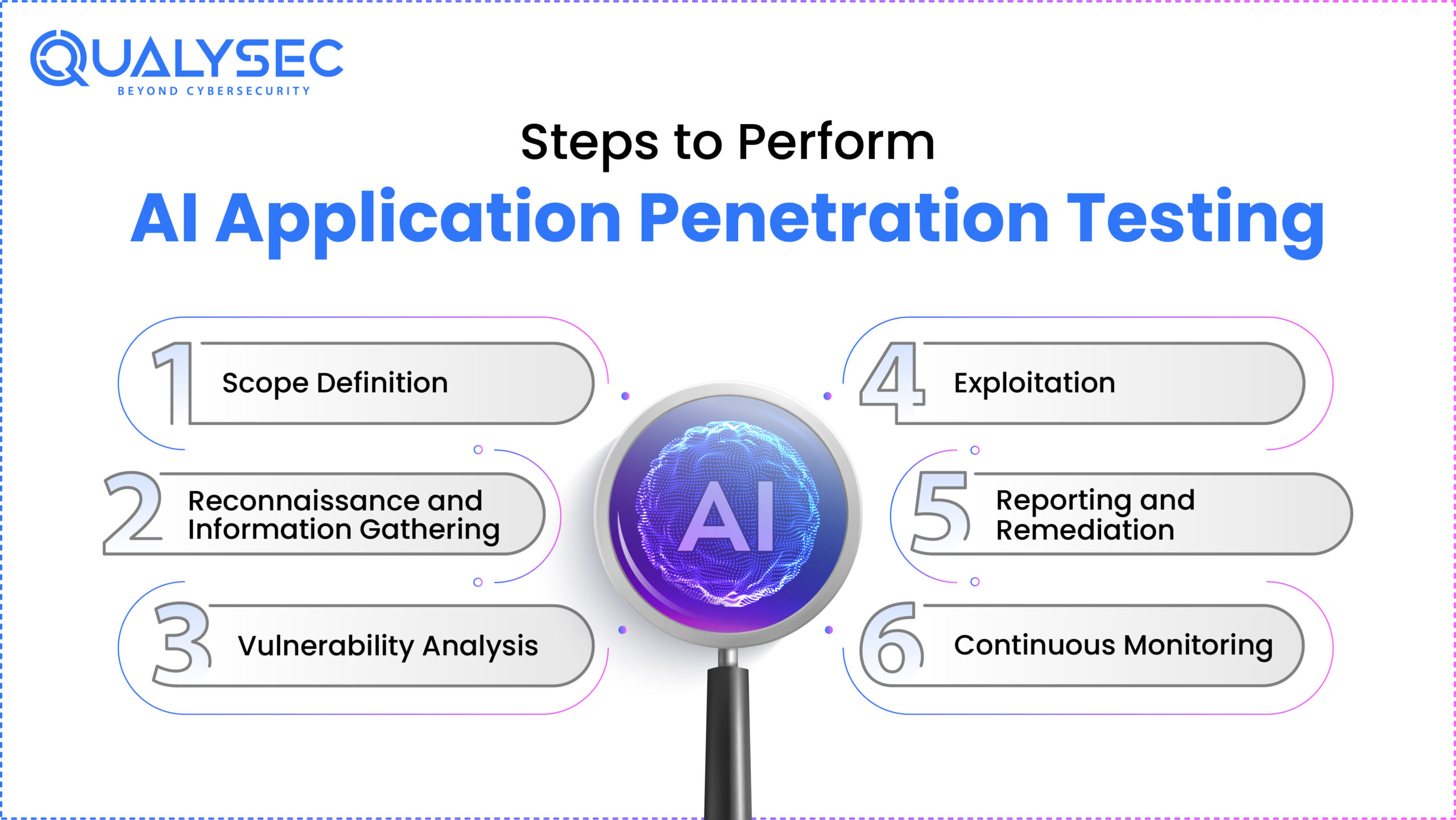

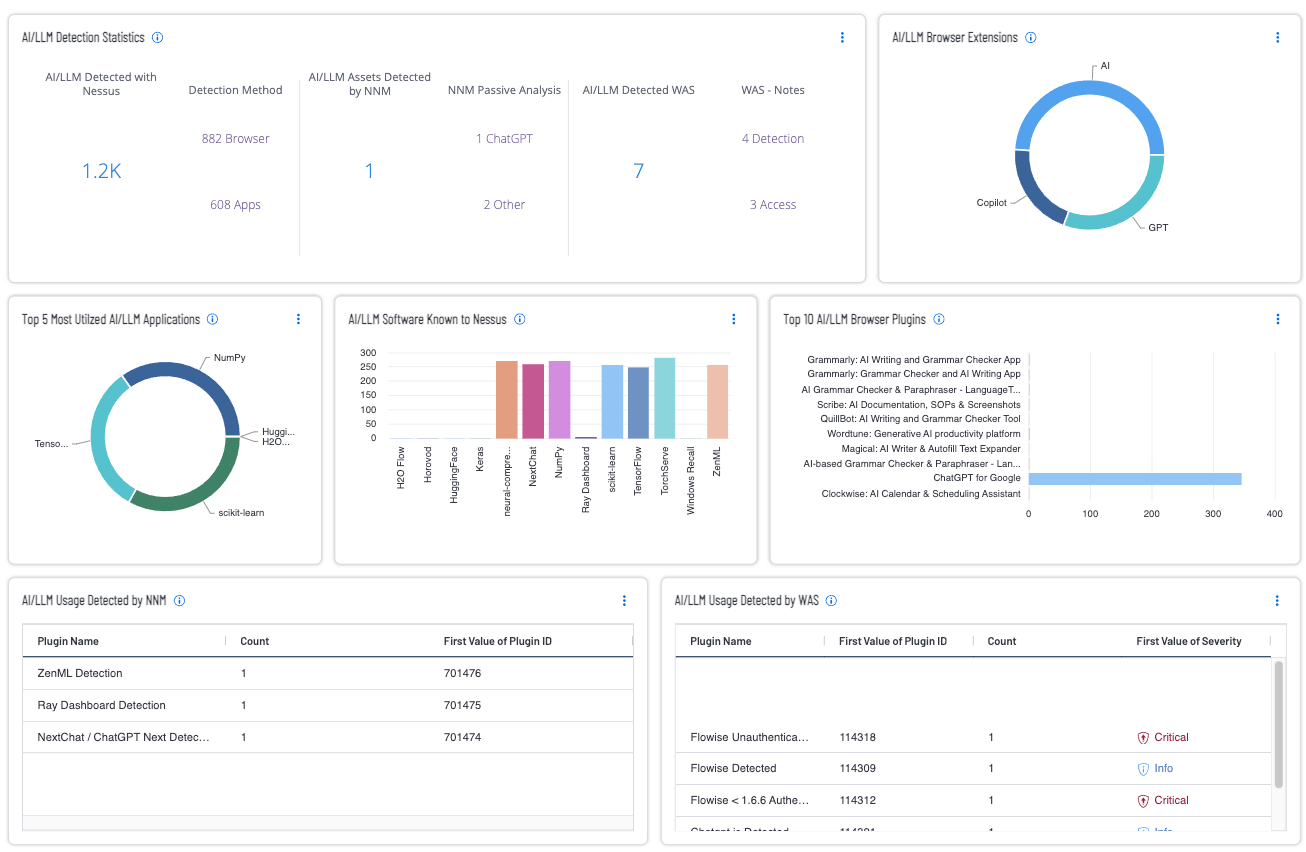
In the world of cybersecurity, penetration testing (or “pentesting”) has long been a cornerstone of proactive defence. It’s the process where skilled humans simulate attacks on systems, networks, and applications to uncover vulnerabilities before malicious actors do. Today, however, we’re witnessing a major shift: artificial intelligence (AI) is now playing an increasingly critical role in pentesting.
Why is AI Becoming Relevant for Penetration Testing?
Several forces are driving the integration of AI into penetration testing:
- Complexity & Speed: Modern IT ecosystems—cloud, IoT, microservices—are vast and dynamic. Manual testing can’t keep pace.
- AI’s Pattern Recognition: AI can automate reconnaissance, analyze massive data sets, and predict potential exploit paths.
- Continuous Testing: Organizations demand ongoing visibility rather than quarterly scans; AI enables near real-time security assessments.
How AI-Powered Penetration Testing Works
Traditional pentests follow stages like scoping, reconnaissance, exploitation, and reporting. AI augments each phase by automating repetitive steps and discovering patterns invisible to humans.
- Reconnaissance: AI agents parse DNS data, cloud logs, and endpoints faster than humans ever could.
- Vulnerability Discovery: Beyond CVEs, AI detects misconfigurations and new exploit chains.
- Exploitation: AI can simulate chained attacks or lateral movement scenarios autonomously.
- Reporting: AI tools summarize findings with prioritized risk context and remediation steps.
Key Benefits of AI in Pentesting
- Scale and Coverage: Continuous AI-driven testing reduces blind spots.
- Speed: Automation delivers faster discovery-to-remediation cycles.
- Enhanced Focus: Human testers can focus on high-level logic flaws while AI handles routine scans.
- Integration: AI testing aligns easily with CI/CD pipelines and DevSecOps workflows.
Risks and Limitations
AI doesn’t eliminate the need for human expertise. In fact, it introduces new challenges:
- False Positives: AI may hallucinate or overestimate risks without context.
- Ethical Oversight: Autonomous agents must be strictly controlled to prevent unauthorized testing.
- Business Logic Gaps: AI struggles with nuanced, context-heavy attack paths requiring human creativity.
- AI-Specific Risks: Pentesting must now cover prompt injections, model theft, and adversarial attacks.
Adopting AI-Augmented Penetration Testing
- Define Scope: Determine whether you’re testing infrastructure, applications, or AI models themselves.
- Select Tools + Experts: Combine AI-driven tools with human pentesters for maximum accuracy.
- Integrate with DevSecOps: Automate testing triggers during deployments or configuration changes.
- Governance: Establish strict rules of engagement and maintain logs for transparency.
- Upskill Teams: Train security professionals in AI-driven methodologies and LLM vulnerability testing.
The Future of AI in Penetration Testing
- Autonomous Pentesting: Tools like NodeZero and Xbow demonstrate AI agents that test and exploit networks autonomously.
- AI vs. AI Warfare: As attackers adopt AI, defenders must counter with their own intelligent systems.
- Standardization: Expect new frameworks for ethical AI pentesting and AI-system safety validation.
- Human–AI Collaboration: The future is hybrid—AI handles scale; humans handle strategy and creativity.
Conclusion
AI isn’t replacing penetration testers—it’s enhancing them. The combination of AI automation and human insight enables deeper, faster, and more continuous security validation. Organizations that intelligently adopt AI in their pentesting strategy will gain resilience against increasingly automated and adaptive threats.
Ready to explore AI-powered pentesting for your organization? Stay tuned for our upcoming post: “How to Build an AI-Augmented Pentest Framework.”
Written by: Cybersecurity Insights Team
Published on: November 12, 2025
Comments
Post a Comment